GRE over IPsec Site to Site VPN
IPsec Tunnel könne nur unicast Traffic transportieren, damit aber auch Multicast und Broadcast Traffic übertragen werden können, legt man in den IPsec Tunnel “einfach” einen GRE Tunnel
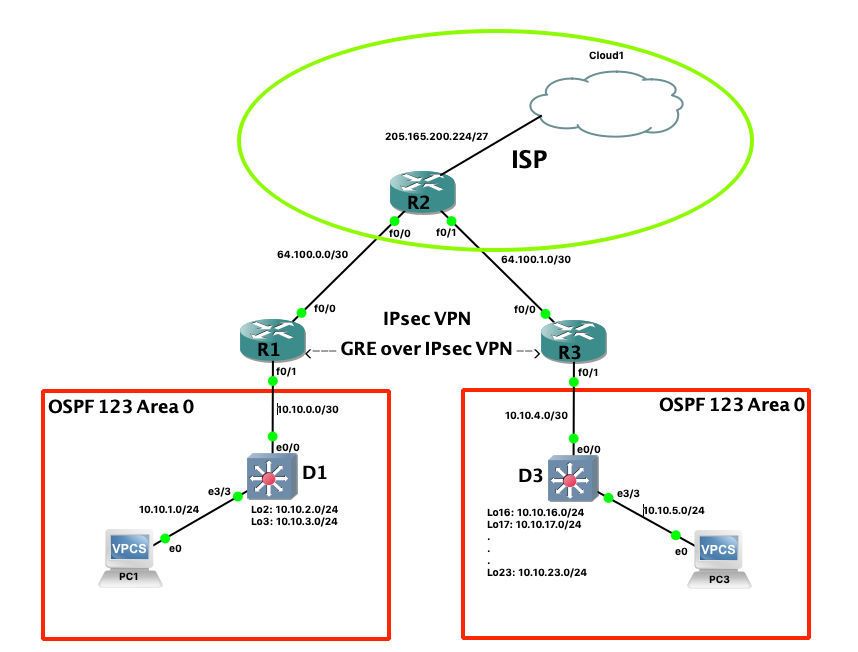
Die Grundkonfiguration der Geräte
R1
interface Loopback2
ip address 10.10.2.1 255.255.255.0
!
interface Loopback3
ip address 10.10.3.1 255.255.255.0
!
interface FastEthernet0/0
ip address 64.100.0.2 255.255.255.252
duplex auto
speed auto
crypto map GRE-CMAP
!
interface FastEthernet0/1
ip address 10.10.0.1 255.255.255.252
duplex auto
speed auto
!
router ospf 123
router-id 1.1.1.1
log-adjacency-changes
auto-cost reference-bandwidth 1000
network 10.10.0.0 0.0.0.3 area 0
default-information originate
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 64.100.0.1
!
R2
interface Loopback0
ip address 209.165.200.225 255.255.255.224
!
interface FastEthernet0/0
ip address 64.100.0.1 255.255.255.252
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 64.100.1.1 255.255.255.252
duplex auto
speed auto
!
ip route 0.0.0.0 0.0.0.0 Loopback0
ip route 10.10.0.0 255.255.252.0 64.100.0.2
ip route 10.10.4.0 255.255.252.0 64.100.1.2
ip route 10.10.16.0 255.255.248.0 64.100.1.2
!
R3
interface Loopback16
ip address 10.10.16.1 255.255.255.0
!
interface Loopback17
ip address 10.10.17.1 255.255.255.0
!
interface Loopback18
ip address 10.10.18.1 255.255.255.0
!
interface Loopback19
ip address 10.10.19.1 255.255.255.0
!
interface Loopback20
ip address 10.10.20.1 255.255.255.0
!
interface Loopback21
ip address 10.10.21.1 255.255.255.0
!
interface Loopback22
ip address 10.10.22.1 255.255.255.0
!
interface Loopback23
ip address 10.10.23.1 255.255.255.0
!
interface FastEthernet0/0
ip address 64.100.1.2 255.255.255.252
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 10.10.4.1 255.255.255.252
duplex auto
speed auto
!
router ospf 123
router-id 3.3.3.3
log-adjacency-changes
auto-cost reference-bandwidth 1000
network 10.10.4.0 0.0.0.3 area 0
default-information originate
!
ip route 0.0.0.0 0.0.0.0 64.100.1.1
!
PC 1
IP: 10.10.1.10
Mask: 255.255.255.0
GW: 10.10.1.1
PC2
IP: 10.10.5.10
MASK: 255.255.255.0
GW: 10.10.5.1
D1
interface Loopback2
ip address 10.10.2.1 255.255.255.0
!
interface Loopback3
ip address 10.10.3.1 255.255.255.0
!
interface Ethernet0/0
no switchport
ip address 10.10.0.2 255.255.255.252
duplex auto
!
interface Ethernet3/3
no switchport
ip address 10.10.1.1 255.255.255.0
duplex auto
!
interface Vlan1
no ip address
shutdown
!
router ospf 123
router-id 1.1.1.2
auto-cost reference-bandwidth 1000
network 10.10.0.0 0.0.3.255 area 0
!
D3
interface Loopback16
ip address 10.10.16.1 255.255.255.0
!
interface Loopback17
ip address 10.10.17.1 255.255.255.0
!
interface Loopback18
ip address 10.10.18.1 255.255.255.0
!
interface Loopback19
ip address 10.10.19.1 255.255.255.0
!
interface Loopback20
ip address 10.10.20.1 255.255.255.0
!
interface Loopback21
ip address 10.10.21.1 255.255.255.0
!
interface Loopback22
ip address 10.10.22.1 255.255.255.0
!
interface Loopback23
ip address 10.10.23.1 255.255.255.0
!
interface Ethernet0/0
no switchport
ip address 10.10.4.2 255.255.255.252
duplex auto
!
interface Ethernet3/3
no switchport
ip address 10.10.5.1 255.255.255.0
duplex auto
!
interface Vlan1
no ip address
shutdown
!
router ospf 123
router-id 3.3.3.2
auto-cost reference-bandwidth 1000
network 10.10.4.0 0.0.1.255 area 0
network 10.10.16.0 0.0.0.7 area 0
!
Die Tunnel Konfiguration
R1
crypto isakmp policy 10
encryption aes 256
hash sha
authentication pre-share
group 1
lifetime 3600
!
crypto isakmp key 0 cisco123 address 64.100.1.2 <– Passwort und Gegenstelle von der das Passowrt erwartet wird
!
!
crypto ipsec transform-set GRE-VPN esp-aes 256 esp-sha-hmac <– transform set erstellen
mode transport
!
ip access-list extended GRE-VPN-ACL
permit gre host 64.100.0.2 host 64.100.1.2
!
crypto map GRE-CMAP 10 ipsec-isakmp
set peer 64.100.1.2
set transform-set GRE-VPN <- erstelltes Transformset
match address GRE-VPN-ACL <- vorher erstelle ACL
!
int f0/0
crypto map GRE-CMAP <– Map an Interface binden
!
interface Tunnel0
ip address 172.16.1.1 255.255.255.252
tunnel source 64.100.0.2
tunnel destination 64.100.1.2
!
router ospf 123
network 172.16.1.0 0.0.0.3 area 0 <– Tunnel IP ins OSPF aufnehmen
!
R2
crypto isakmp policy 10
encryption aes 256
hash sha
authentication pre-share
group 1
lifetime 3600
!
crypto isakmp key 0 cisco123 address 64.100.0.2 <– Passwort und Gegenstelle von der das Passwort erwartet wird
!
crypto ipsec transform-set GRE-VPN esp-aes 256 esp-sha-hmac <– transform set erstellen
mode transport
!
crypto ipsec profile GRE-PROFILE <– IPsec Profil erstellen
set transform-set GRE-VPN
!
interface Tunnel0
ip address 172.16.1.2 255.255.255.252
tunnel source 64.100.1.2
tunnel destination 64.100.0.2
tunnel protection ipsec profile GRE-PROFILE
!
router ospf 123
network 172.16.1.0 0.0.0.3 area 0 <– Tunnel IP ins OSPF aufnehmen
!
Befehle zum überprüfen
– show interface tunnel 0
– show crypto ipsec sa
– show crypto session
– show ip ospf interface brief
– show ip ospf neighbor
– sh ip route ospf

