Zone-Based Policy Firewall
Hier geht es darum eine Zonenbasierende Firewall auf einem Router zu erstellen.
Es gibt die Zonen
– Internet
– ConfRoom
– Inside
Die Kommunikation soll folgendermassen möglich sein :
Aus dem Confroom nur per HTTP/HTTPS/DNS in Richtung Internet zum Webserver
Aus der Inside Zone soll TCP/UDP und ICMP möglich sein
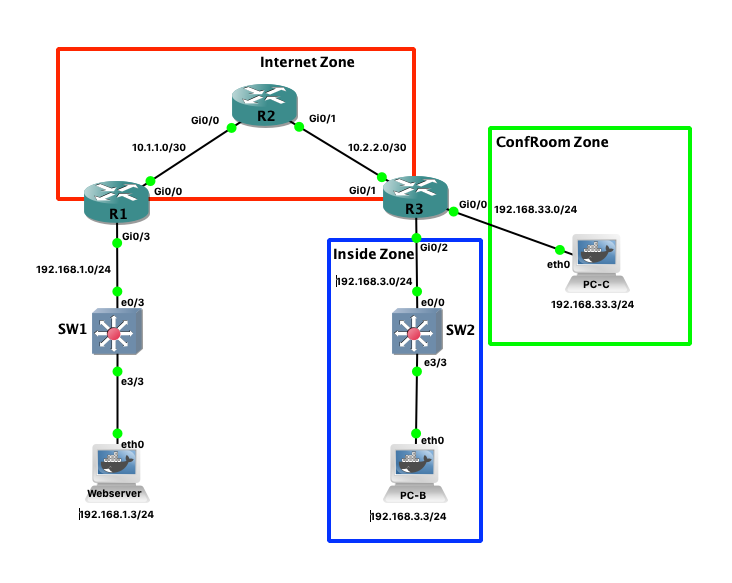
Zu erste müssen die Router so konfiguriert werden, das sie alle Clients untereinander erreichen können
R1
!
hostname R1
!
interface GigabitEthernet0/0
ip address 10.1.1.1 255.255.255.252
duplex auto
speed auto
media-type rj45
!
interface GigabitEthernet0/3
ip address 192.168.1.1 255.255.255.0
duplex auto
speed auto
media-type rj45
!
ip route 0.0.0.0 0.0.0.0 10.1.1.2
R2
!
hostname R2
!
interface GigabitEthernet0/0
ip address 10.1.1.2 255.255.255.252
duplex auto
speed auto
media-type rj45
!
interface GigabitEthernet0/1
ip address 10.2.2.2 255.255.255.252
duplex auto
speed auto
media-type rj45
!
ip route 192.168.1.0 255.255.255.0 10.1.1.1
ip route 192.168.3.0 255.255.255.0 10.2.2.1
ip route 192.168.33.0 255.255.255.0 10.2.2.1
R3
!
hostname R3
!
interface GigabitEthernet0/0
ip address 192.168.33.1 255.255.255.0
duplex auto
speed auto
media-type rj45
!
interface GigabitEthernet0/1
ip address 10.2.2.1 255.255.255.252
duplex auto
speed auto
media-type rj45
!
interface GigabitEthernet0/2
ip address 192.168.3.1 255.255.255.0
duplex auto
speed auto
media-type rj45
!
ip route 0.0.0.0 0.0.0.0 10.2.2.2
Wenn sie alle Clients gegenseitig anpingen können, dann passt das Routing
Jetzt geht es an die Konfiguration der Zonen Firewall
Zonen anlegen
zone security INSIDE
zone security CONFROOM
zone security INTERNET
Festlegen in welcher Class Map auf was gefiltert werden soll
class-map type inspect match-any INSIDE_PROTOCOLS
match protocol tcp
match protocol udp
match protocol icmp
!
class-map type inspect match-any CONFROOM_PROTOCOLS
match protocol http
match protocol https
match protocol dns
!
Class Map an die Policy Map binden
policy-map type inspect INSIDE_TO_INTERNET
class type inspect INSIDE_PROTOCOLS
inspect
policy-map type inspect CONFROOM_TO_INTERNET
class type inspect CONFROOM_PROTOCOLS
inspect
!
Source und Destination der Zonen festlegen und dieser Verbindung einen Namen geben
!
zone-pair security INSIDE_TO_INTERNET source INSIDE destination INTERNET
!
zone-pair security CONFROOM_TO_INTERNET source CONFROOM destination INTERNET
!
Policy Maps an die Zone-pairs binden
zone-pair security INSIDE_TO_INTERNET source INSIDE destination INTERNET
service-policy type inspect INSIDE_TO_INTERNET
!
zone-pair security CONFROOM_TO_INTERNET source CONFROOM destination INTERNET
service-policy type inspect CONFROOM_TO_INTERNET
!
Kontrolle der Zone-pair Bindung
R3(config)#do sh zone-pair security
Zone-pair name INSIDE_TO_INTERNET
Source-Zone INSIDE Destination-Zone INTERNET
service-policy INSIDE_TO_INTERNET
Zone-pair name CONFROOM_TO_INTERNET
Source-Zone CONFROOM Destination-Zone INTERNET
service-policy CONFROOM_TO_INTERNET
Jetzt werden die Zonen an die entsprechenden Interfaces gebunden
!
interface GigabitEthernet0/0
zone-member security CONFROOM <– Zone an das Interface binden
!
interface GigabitEthernet0/1
zone-member security INTERNET <– Zone an das Interface binden
!
interface GigabitEthernet0/2
zone-member security INSIDE <– Zone an das Interface binden
!
Kontrolle der Zonen, welches Interface gehört zu welcher Zone
R3#sh zone security
zone self
Description: System Defined Zone
zone INSIDE
Member Interfaces:
GigabitEthernet0/2
zone CONFROOM
Member Interfaces:
GigabitEthernet0/0
zone INTERNET
Member Interfaces:
GigabitEthernet0/1
R3#show policy-map type inspect zone-pair
policy exists on zp INSIDE_TO_INTERNET
Zone-pair: INSIDE_TO_INTERNET
Service-policy inspect : INSIDE_TO_INTERNET
Class-map: INSIDE_PROTOCOLS (match-any)
Match: protocol tcp
0 packets, 0 bytes
30 second rate 0 bps
Match: protocol udp
0 packets, 0 bytes
30 second rate 0 bps
Match: protocol icmp
2 packets, 128 bytes
30 second rate 0 bps
Inspect
Packet inspection statistics [process switch:fast switch]
icmp packets: [12:0]
Session creations since subsystem startup or last reset 2
Current session counts (estab/half-open/terminating) [0:0:0]
Maxever session counts (estab/half-open/terminating) [2:1:0]
Last session created 00:26:44
Last statistic reset never
Last session creation rate 0
Maxever session creation rate 2
Last half-open session total 0
TCP reassembly statistics
received 0 packets out-of-order; dropped 0
peak memory usage 0 KB; current usage: 0 KB
peak queue length 0
Class-map: class-default (match-any)
Match: any
Drop
0 packets, 0 bytes
policy exists on zp CONFROOM_TO_INTERNET
Zone-pair: CONFROOM_TO_INTERNET
Service-policy inspect : CONFROOM_TO_INTERNET
Class-map: CONFROOM_PROTOCOLS (match-any)
Match: protocol http
1 packets, 40 bytes
30 second rate 0 bps
Match: protocol https
0 packets, 0 bytes
30 second rate 0 bps
Match: protocol dns
0 packets, 0 bytes
30 second rate 0 bps
Inspect
Packet inspection statistics [process switch:fast switch]
tcp packets: [50:0]
Session creations since subsystem startup or last reset 1
Current session counts (estab/half-open/terminating) [0:0:0]
Maxever session counts (estab/half-open/terminating) [1:1:1]
Last session created 00:32:10
Last statistic reset never
Last session creation rate 0
Maxever session creation rate 1
Last half-open session total 0
TCP reassembly statistics
received 0 packets out-of-order; dropped 0
peak memory usage 0 KB; current usage: 0 KB
peak queue length 0
Class-map: class-default (match-any)
Match: any
Drop
22 packets, 1408 bytes


