Site to Site ipsec VPN
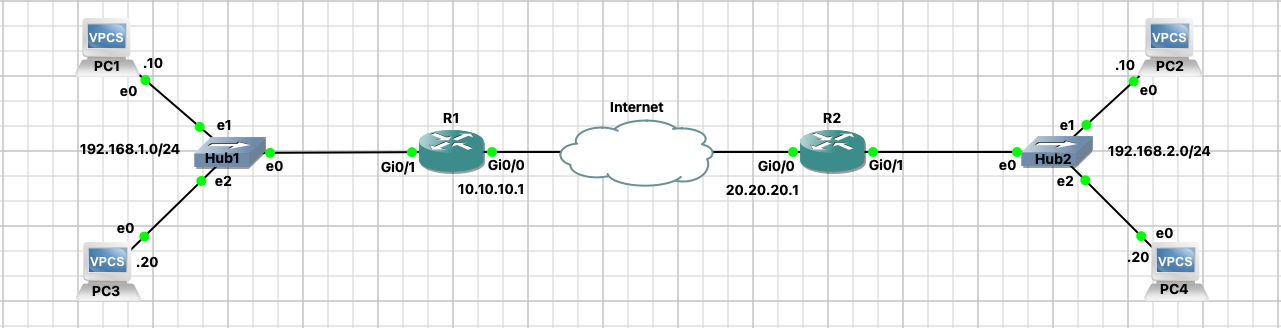
Welcher Traffic ist über das WAN Interface erlaubt
R1
!
ip access-list extended VPN-ACL
permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
!
R2
!
ip access-list extended VPN-ACL
permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
!
Welcher Traffic wird beim NAT berücksichtigt
R1
!
ip access-list extended NAT-ACL
deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
permit ip 192.168.1.0 0.0.0.255 any
!
R2
!
ip access-list extended NAT-ACL
deny ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
permit ip 192.168.2.0 0.0.0.255 any
!
Jetzt das ganze zusammen bauen
R1
!
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key secretkey address 20.20.20.1
!
crypto ipsec transform-set TRSET esp-3des esp-md5-hmac
mode tunnel
!
crypto map VPNMAP 10 ipsec-isakmp
set peer 20.20.20.1
set transform-set TRSET
match address VPN-ACL
!
interface GigabitEthernet0/0
ip address 10.10.10.1 255.255.255.0
ip nat outside
ip virtual-reassembly in
duplex auto
speed auto
media-type rj45
crypto map VPNMAP
!
interface GigabitEthernet0/1
ip address 192.168.1.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
duplex auto
speed auto
media-type rj45
!
R2
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key secretkey address 10.10.10.1
!
crypto ipsec transform-set TRSET esp-3des esp-md5-hmac
mode tunnel
!
crypto map VPNMAP 10 ipsec-isakmp
set peer 10.10.10.1
set transform-set TRSET
match address VPN-ACL
!
interface GigabitEthernet0/0
ip address 20.20.20.1 255.255.255.0
ip nat outside
ip virtual-reassembly in
duplex auto
speed auto
media-type rj45
crypto map VPNMAP
!
interface GigabitEthernet0/1
ip address 192.168.2.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
duplex auto
speed auto
media-type rj45
!
Das ganze testen
R1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
20.20.20.1 10.10.10.1 QM_IDLE 1001 ACTIVE
IPv6 Crypto ISAKMP SA
R2#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
20.20.20.1 10.10.10.1 QM_IDLE 1001 ACTIVE
IPv6 Crypto ISAKMP SA
R1#show crypto ipsec sa
interface: GigabitEthernet0/0
Crypto map tag: VPNMAP, local addr 10.10.10.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
current_peer 20.20.20.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 5, #pkts encrypt: 5, #pkts digest: 5
#pkts decaps: 5, #pkts decrypt: 5, #pkts verify: 5
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 10.10.10.1, remote crypto endpt.: 20.20.20.1
plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0
current outbound spi: 0xEF3680AD(4013326509)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x3E59DC27(1046076455)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, sibling_flags 80004040, crypto map: VPNMAP
sa timing: remaining key lifetime (k/sec): (4296050/2264)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xEF3680AD(4013326509)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, sibling_flags 80004040, crypto map: VPNMAP
sa timing: remaining key lifetime (k/sec): (4296050/2264)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
R2#sh crypto ipsec sa
interface: GigabitEthernet0/0
Crypto map tag: VPNMAP, local addr 20.20.20.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
current_peer 10.10.10.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 5, #pkts encrypt: 5, #pkts digest: 5
#pkts decaps: 5, #pkts decrypt: 5, #pkts verify: 5
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 20.20.20.1, remote crypto endpt.: 10.10.10.1
plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0
current outbound spi: 0x3E59DC27(1046076455)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xEF3680AD(4013326509)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, sibling_flags 80000040, crypto map: VPNMAP
sa timing: remaining key lifetime (k/sec): (4308842/2232)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x3E59DC27(1046076455)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, sibling_flags 80000040, crypto map: VPNMAP
sa timing: remaining key lifetime (k/sec): (4308842/2232)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:

